Describe the Steps in the Information System Security Audit Process
Define the scope of an audit. Decisions need to be made in groups.
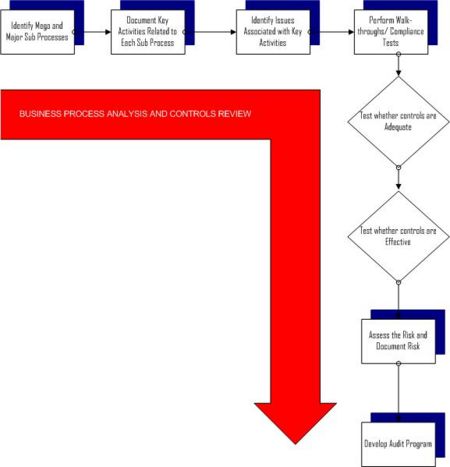
Information Systems Audit Methodology Wikieducator
An automated audit is a computer-assisted audit technique also known as a CAAT.

. The various activities involved in defining an audit program include audit checklists resource planning and consistency in tests. Audit steps performed and audit evidence gathered Use of services of other auditors and experts Audit findings conclusions and recommendations The documentation should also include evidence of supervisory review and the report that was issued as a result of the audit work. The first thing you need to do is to establish the scope of your audit.
Perform the auditing work. Identify threats Next look at the assets you plan to audit and list the potential threats next to each one. Audits can have different purposes.
Here are details of activities that you will be doing in each step of auditing process. This stage may require the auditors to look through relevant business documents and previous audit results. What counts as a threat.
Audit Process Flowchart Below is the audit process flowchart that shows an overview of auditing and the main stages of audit. Save Time Money - Start Now. There is a wide range of activities that go past simply managing the security and privacy.
During this type of audit the auditor will interview your employees conduct security and vulnerability scans evaluate physical access to systems and analyze your application and operating system access controls. Ad Easily Find The Audit Systems Youre Looking For w Our Comparison Grid. However those audit steps can be categorized into the main stages of audit including the planning stage audit evidence-gathering stage and completion stage which is the final stage of audit where we can issue the report.
Primarily this is a four stage process. I think the risk decisions at Levels 1 and 2 can impact a selection and implementation of controls greatly. Its unlikely that youll be able to audit all your assetsso the final part of this step is determining which assets youll audit and which you wont.
There are five phases of our audit process. 10 Steps of the Audit Process An audit is an objective analysis and examination of some aspect of a companys operations to confirm the extent to which the organization is in compliance with expected standards. Various techniques used by the auditors include audit area selection simulation and modeling scoring and competency center.
Step 1 the selection phase. Communicate emerging issues potential risks and audit results to your key stakeholders. So IS auditors also follow the auditing process that other auditors do.
In this article we will name this the professional auditing process. A financial audit looks at a companys financial records to make sure theyre correct. Use generated documentation to verify that the routines practiced in the company match what the auditor defined in the process flow.
Selection Planning Execution Reporting and Follow-Up. Conduct audits in accordance with IS audit standards guidelines and best practices to meet your planned audit objectives. The Process of Auditing Information Systems - Part 1 start the course recognize the task and knowledge statements of domain 1 describe characteristics of the IS audit function identify best practices in IS audit resource management identify best practices for planning audits identify the effects of laws and regulations on IS audit planning.
The risk assessment should cover the following steps. Internal Controls are Analyzed In this step system auditors determine the efficacy of the information systems internal controls and whether or not they are working the way they should. 4 Simple steps to self-audit.
Whether you check the general state of security in your organization or do a specific network security audit third party security audit or any other you need to know what you should look at and what you should skip. Identify and locate the exact assets located within the security perimeter and. Provide a reason why you think the risk decisions at Levels 1 and 2 can impact the selection and implementation of controls at the System level.
You should document the process through a flow of procedures and controls. Create a list of action items based on the audit and prioritize fixes and changes to remediate the security. The auditor should indicate points where possible process improvements can be developed.
Complete the audit and socialize the results with all of the stakeholders using the agreed-upon definitions from the earlier steps. Review the Best Audit Systems for 2022. Preparing an audit program is the first step of conducting an information systems audit.
A risk assessment is carried out to develop an audit plan. Plan specific audits to ensure that your IT and business systems are protected and controlled. They also check any missing internal controls within the.
Define the Objectives Lay out the goals that the auditing team aims to achieve by conducting the IT security audit. We develop the audit plan for the subsequent year based on the results of this assessment and the departments available resources. The Steps in an IT Security Audit A cyber security audit consists of five steps.
Selection Phase Internal Audit conducts a University-wide risk assessment near the end of each calendar year. Step 2 the planning phase.

It Security Audit Checklist Template Inspirational Security Audit Information Security Audit Checklist Xls Internal Audit Checklist Template Security Audit

Imsxpress Iso 9001 Internal Audit Checklist Quality Management Imsxpress Sampleresume Audittemplates Internal Audit Checklist Template Report Template
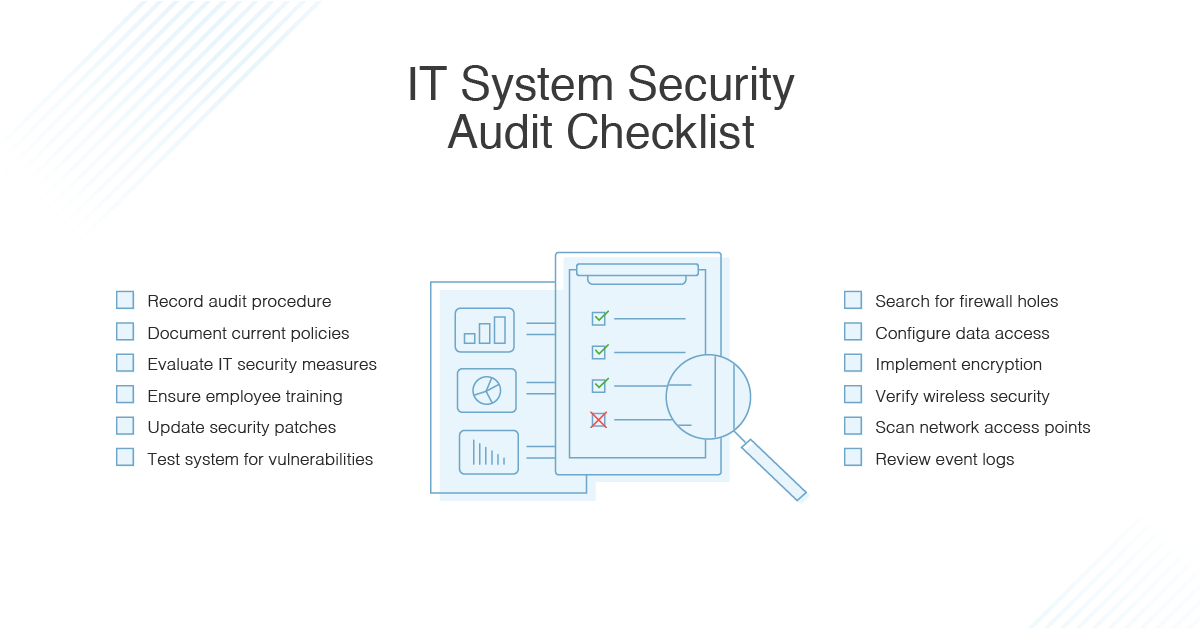
It Security Audit Standards Best Practices And Tools Dnsstuff

5 In Demand Cyber Security Certifications Techroots Cyber Security Certifications Cyber Security Data Security

Itil Information Security Management Risk Analysis Internal Audit Self Assessment

Cyber Security Program Strategies For Beginners Cyber Security Program Cyber Security Cyber

Iso 27001 Information Security Templates Sop Risk Sample And Policy Cover Policy Template Standard Operating Procedure Standard Operating Procedure Template

How To Prepare For Iso 27001 Certification Process Step By Step For Auditee Organizations Iso 13485 Risk Management Risk Management Strategies
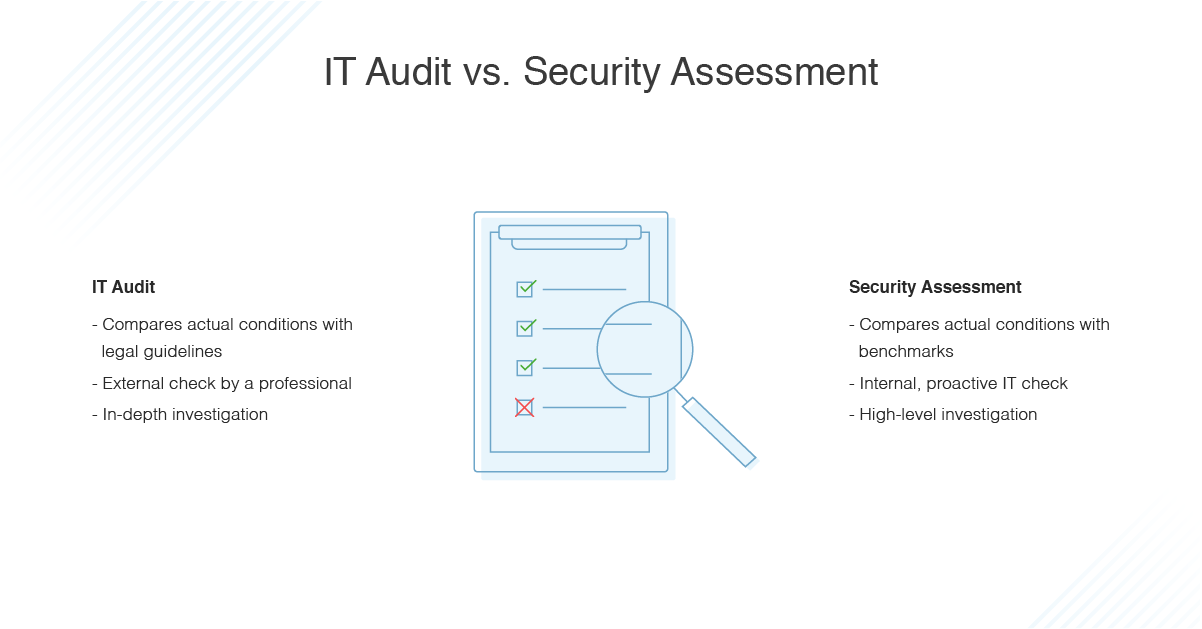
How Does An It Audit Differ From A Security Assessment Dnsstuff

Iso 27001 Internal Audit Checklist Document Kit Covers Iso 27001 Audit Questions Based On Iso 27001 Requirements As Listed Below Internal Audit Audit Checklist

Iso 27001 2013 Information Security Management Isms Hacking Risk Theft Viral Internal Audit Performance Evaluation Risk Management
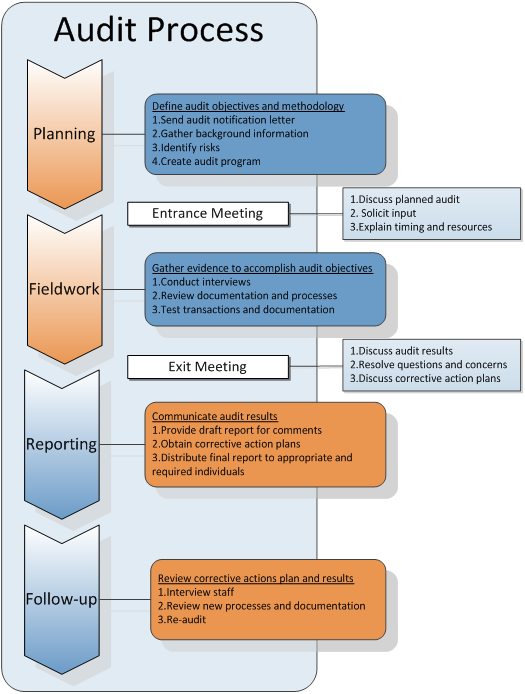
Audit Process Office Of Internal Audits

Best Iso Iec 27001 Implementatin Certification Services Certaim Com Risk Management Internal Audit Cyber Security

Michael Fisher On Twitter Cyber Security Cybersecurity Infographic Computer Security
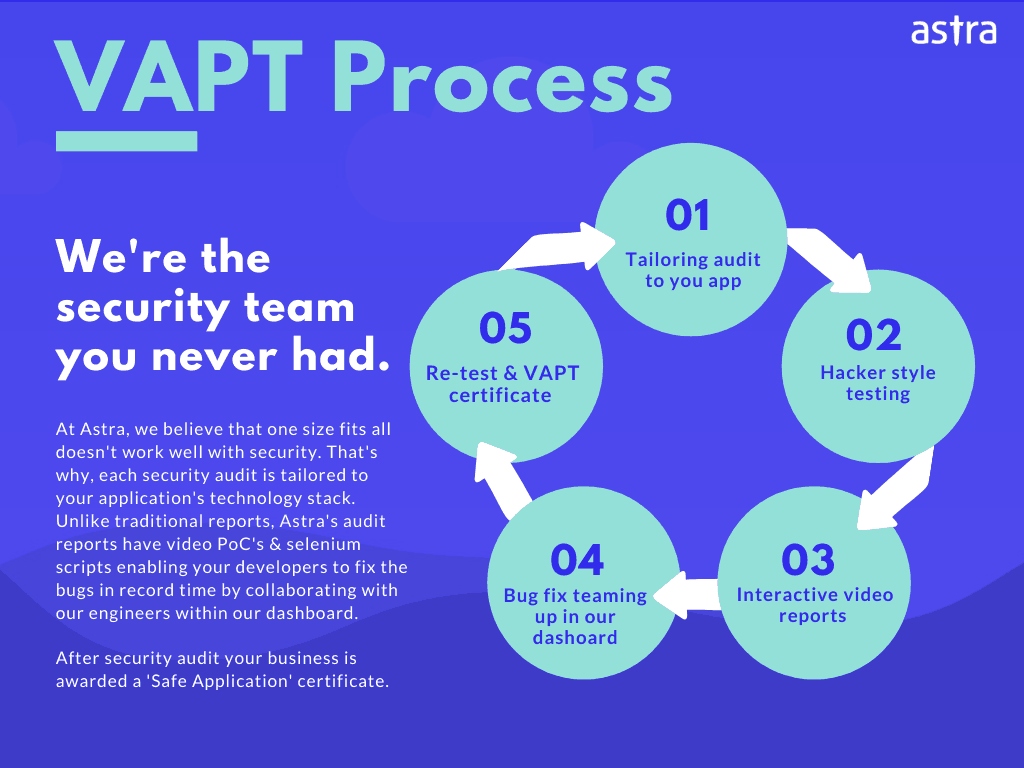
It Security Audit Importance Types And Methodology
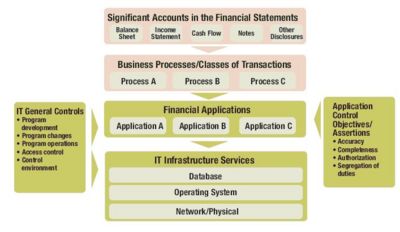
Information Systems Audit Methodology Wikieducator

Physical Security Assessment Template Beautiful Fice Safety Audit Checklist Te Security Assessment Classroom Newsletter Template Preschool Newsletter Templates

Is Audit Basics Developing The It Audit Plan Using Cobit 2019 Isaca Journal

Audit Process 5 Expert Steps For You To Get Your Audit Right Process Street Checklist Workflow And Sop Software
Comments
Post a Comment